Information Security Basic Policy
The Brother Group (the Group) regards information as an important asset for the continuity and growth of its business and recognizes that protecting and properly handling such information ensures the trust of stakeholders and compliance with legal requirements. The Group has established and implemented the Information Security Basic Policy (the Basic Policy) so as to protect all of its information assets from various risks.
1. Compliance with laws, regulations, contracts, and the like
We shall understand and comply with information security-related laws and regulations of each country and contracts with customers, partner companies, and other parties.
2. Establishment of an information security management system
In order to maintain and improve the information security level of the Group, we shall establish internal rules concerning information security and a management system as well as make continuous improvements.
3. Protection of information assets
To protect our information assets from various risks, we shall establish standards for information security management and implement appropriate security measures. In addition, we will continuously review the standards and reflect countermeasures against new risks in the standards.
4. Implementation of education on information security
In order to ensure that all officers and employees involved in information security can perform their work with information security literacy, we shall thoroughly familiarize them with the Basic Policy and continue to implement education on information security.
Representative Director & President
Brother Industries, Ltd.
To ensure that we provide customers with highly safe and secure products so that they can use the purchased products with confidence, we have separately established the Product Information Security Basic Policy.
The Brother Group Information Management System
Information Management Committee
This regulation places the Information Management Committee of Brother Industries, Ltd. (BIL) at the top and clarifies the roles of regional headquarters of Asia, the Americas, Europe, and other regions, as well as Domino, giving them responsibility for information management activities conducted by the subsidiaries under their supervision. This system ensures that decisions made by the Information Management Committee are shared throughout the whole group, and also allows us to grasp the status of information management in the respective subsidiaries.
Information Management Committee Organizational Chart
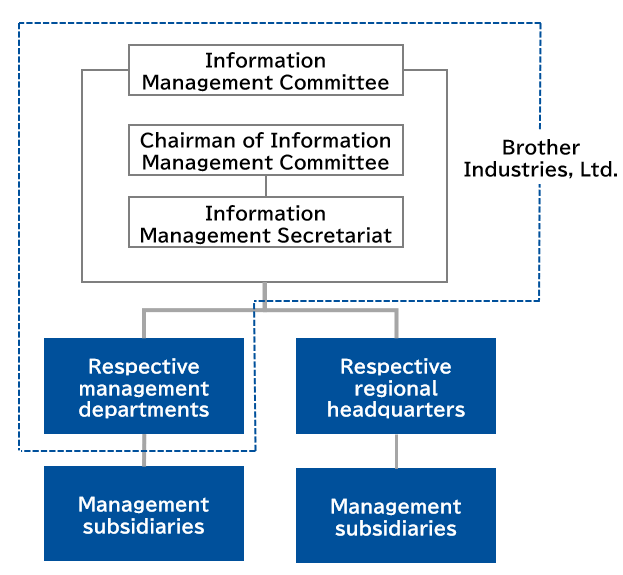
The Information Management Committee holds regular meetings twice a year to deliberate on, give instructions on, and approve the following matters within BIL and the Brother Group:
- Establishment of information management systems and rules related to information management
- Annual plans and performance reports for information management activities
- Responses to any serious incidents related to information management
Information Management
The Brother Group established the Brother Group Information Management Regulation in conformity with the Information Security Management System (ISMS), considering the proper management and protection of information as the basis of maintaining its management quality. The Group therefore manages a wide range of information handled internally according to the unified security criteria that apply to all Group companies. The criteria divide information into four levels based on its confidentiality and lay down rules on the storage, access, and disposition of information for the respective levels, thereby enhancing the security of the information.

Strengthening Measures to Prevent Information Leakage
Measures against unauthorized access from outsiders
Regarding unauthorized access invading from outside the company, we detect suspicious access at three stages, which include entrances from the Internet, the corporate intranet, and exits to the Internet, to prevent information leakage. As countermeasures against targeted attacks by e-mail, we, for example, delete suspicious mails at the entrances from the Internet and monitor and delete malicious programs like computer viruses on the corporate intranet. In addition, communication to dangerous servers is blocked at the exits to the Internet, in order to avoid information leakage.
Measures against internal wrongdoings
We issued the rules for the handling of information in the company and have been disseminating them to our employees through e-learning, etc., to prevent the employees from engaging in risky behavior by mistake.
We install security tools to each PC to manage the usage records and inform employees of this management aiming to prevent their wrongdoings.
External Certification
BIL has obtained ISO/IEC 27001 certification, an international standard for information security management systems, for the following certification registration scope.
| Company name | Brother Industries, Ltd. |
|---|---|
| Certification standard | ISO/IEC 27001:2022 / JIS Q 27001:2023 |
| Certification registration scope |
|
| Certification body | BSI Group Japan K.K. |
| Certification registration No. | IS 812417 |
| Registration date | January 27, 2025 |
| Update date | January 27, 2025 |
| Expiration date | January 26, 2028 |

